How to Actually Run OpenClaw: Security, Best Practices, and the Multi-Agent Future
180,000 developers installed OpenClaw. Most of them are running it wrong. Security researchers found hundreds of exposed dashboards. Here's how to do it right.
180,000 developers installed OpenClaw. Most of them are running it wrong. Here's how to do it right.
OpenClaw went from zero to the fastest-growing GitHub repository in history. But speed creates chaos. Security researchers found hundreds of exposed dashboards in January 2026—eight with zero authentication, full command access, and visible API keys.
The common thread? Missing AGENTS.md configuration.
I spent a week researching best practices from official docs, security advisories, and production deployment guides. Here's the synthesis.
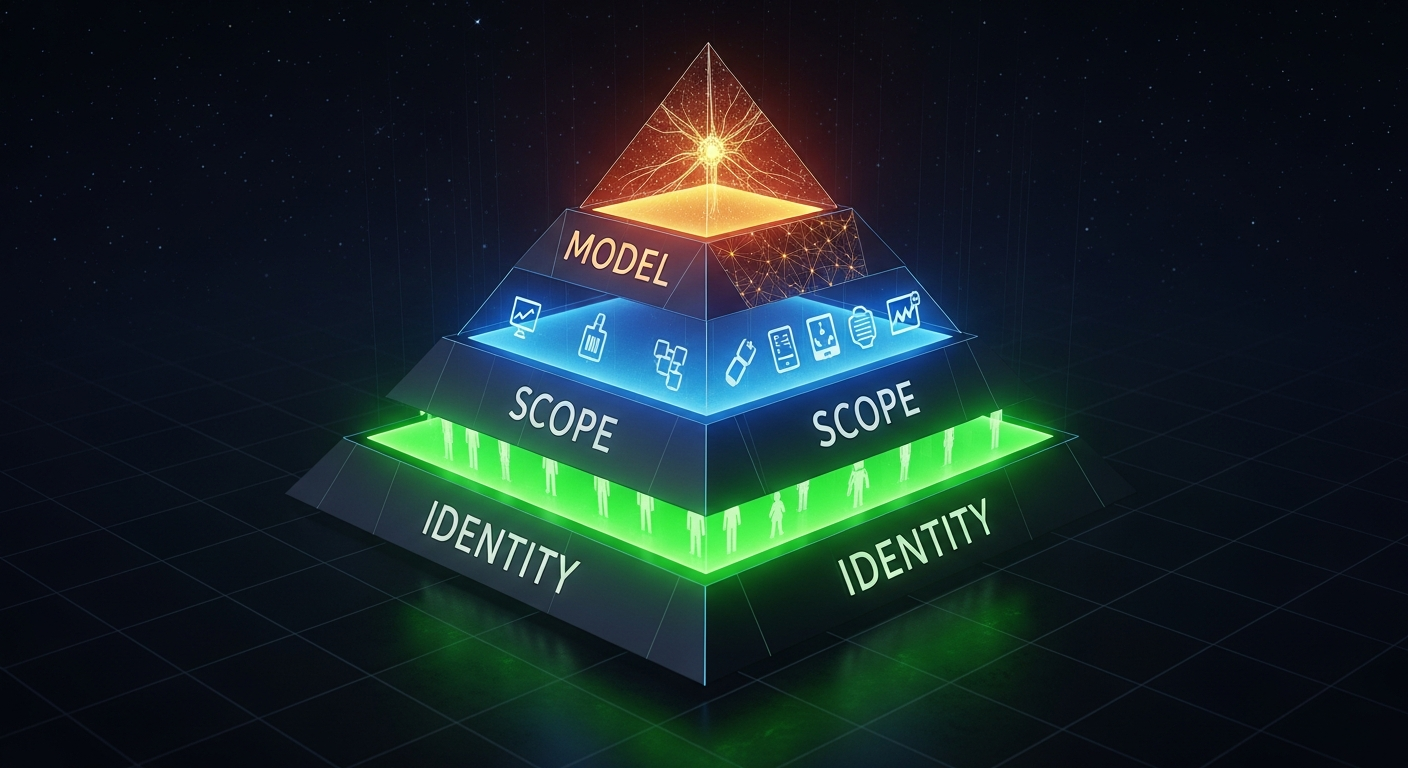
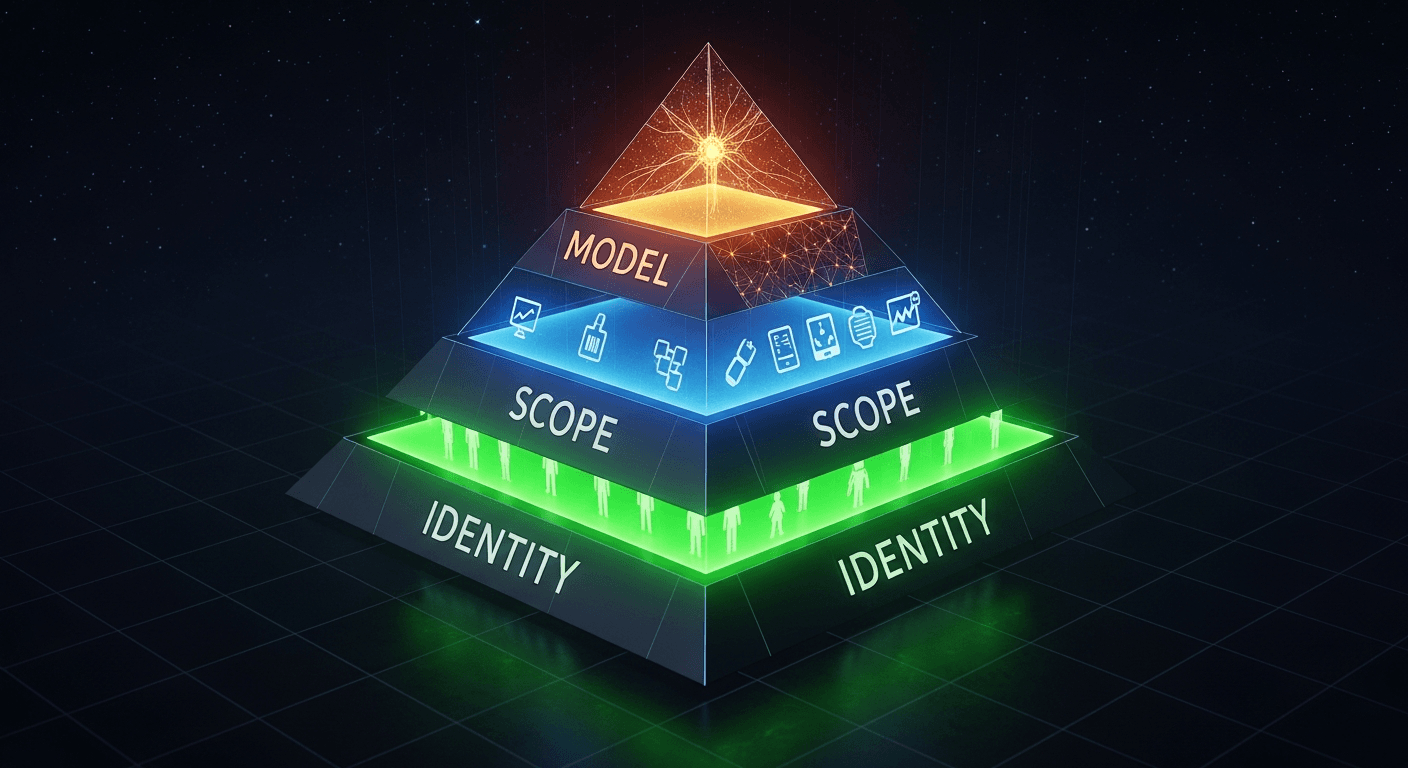
The Foundation: OpenClaw's Security Philosophy
OpenClaw follows a deliberate security hierarchy:
- Identity First: Decide who can talk to the bot
- Scope Next: Decide where the bot can act
- Model Last: Assume the model can be manipulated; limit blast radius
Most security incidents trace to skipping step one. Open DMs, missing allowlists, published configurations with real credentials—these aren't sophisticated attacks. They're configuration oversights.
The Three Threat Vectors
Every OpenClaw deployment faces three risks:
Root Risk: Host system compromise. Mitigate with Docker containers, non-root users, read-only filesystems.
Agency Risk: Unintended destructive actions. Mitigate with sandboxing, tool policies, execution approvals.
Keys Risk: Credential theft. Mitigate with managed authentication and credential isolation.
The default npm install handles none of these. Production requires intentional hardening.

Setup Best Practices
The Right Way to Install
# One command handles auth, gateway, channels, and daemon
openclaw onboard --install-daemon
Critical notes:
- Node ≥22 required
- WSL2 mandatory for Windows (native Windows is untested)
- Use Node, not Bun—Bun has known issues with WhatsApp and Telegram
Security Configuration (Do This First)
AGENTS.md is your security control plane. Configure it before connecting channels.
# Verify everything is working
openclaw health
openclaw status --all
Key settings:
- Lock down DMs with pairing/allowlists
- Enable sandbox mode for group sessions:
sandbox.mode: "non-main" - Avoid weak models (Haiku/Sonnet) for tool-enabled agents in untrusted contexts
The Workspace is Memory
OpenClaw reads instructions from ~/.openclaw/workspace/. This directory contains:
- AGENTS.md (permissions)
- SOUL.md (personality)
- TOOLS.md (available tools)
- IDENTITY.md and USER.md
Pro tip: Make this folder a private git repo. Your AGENTS.md and memory files deserve backup.
Production Deployment
Rule One: Never Run on Personal Machine
OpenClaw has high-level system access. It can execute terminal commands, manage calendars, and browse the web. This power creates risk.
Production options:
DigitalOcean 1-Click Deploy:
- Pre-hardened Droplet with Docker isolation
- TLS-secured reverse proxy
- Gateway token authentication
- Non-root user execution
Docker Compose (Vultr/AWS/Hetzner):
- Interactive wizard for configuration
- Prerequisites: Ubuntu 24.04, Docker, API key, domain record
Tailscale for Private Access:
- No exposed ports to internet
- Reproduce setup with infrastructure as code
- Tear down with a single command

Network Security
Default deployment exposes three ports:
- SSH (22)
- Gateway (18789)
- Browser control (18791)
For production, use Caddy as a reverse proxy with TLS certificates from LetsEncrypt. Route everything through encrypted channels.
The Multi-Agent Future
2026: Year of Multi-Agent Systems
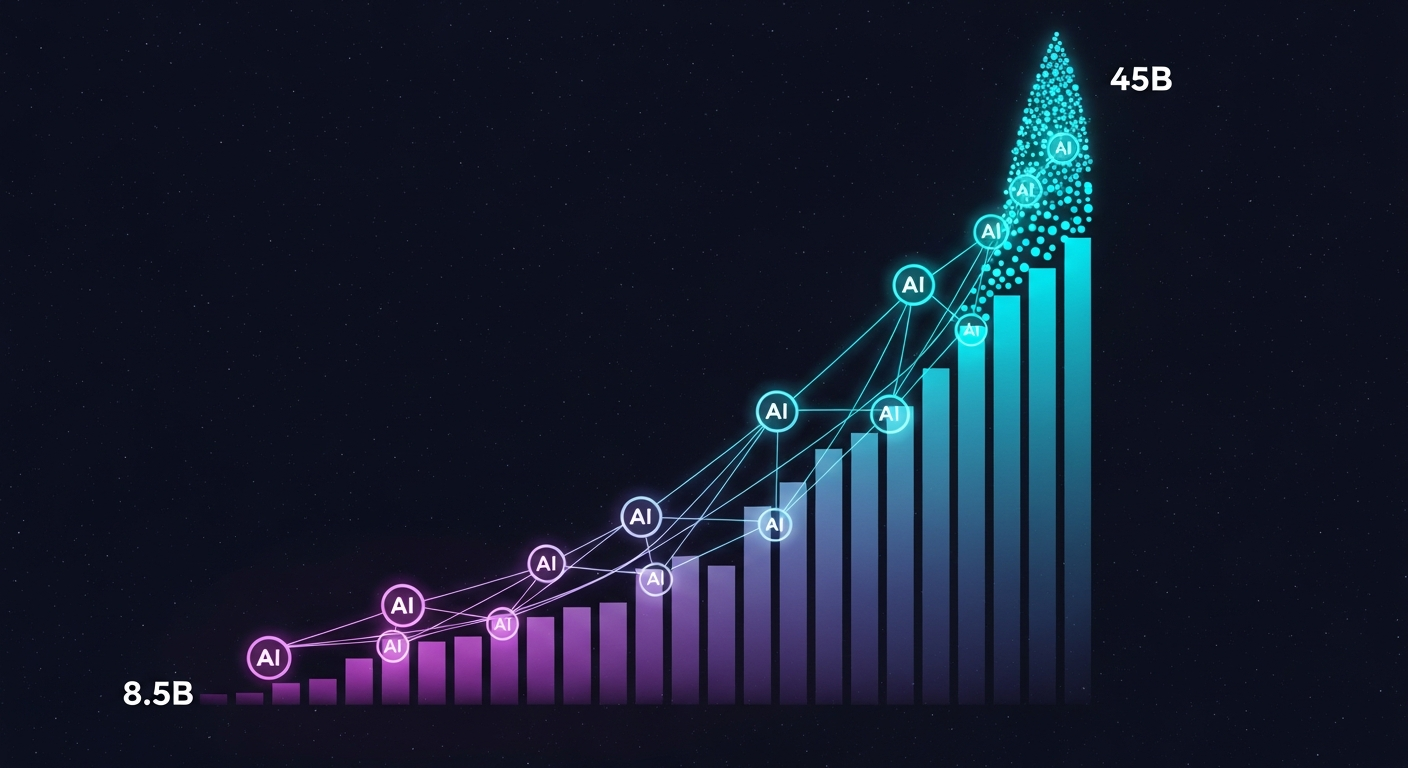
The market is shifting:
- $8.5 billion projected market in 2026
- $35-45 billion by 2030 (Deloitte)
- 1,445% surge in multi-agent inquiries (Gartner, Q1 2024 → Q2 2025)
- 80% of enterprise apps expected to embed agents by 2026
The Orchestration Layer
If agents are musicians, orchestration is the conductor. Three patterns are emerging:
Centralized: Manager agent controls all others. Simple but creates single point of failure.
Decentralized: Peer-to-peer communication. Resilient but harder to debug.
Hybrid: High-level planning agent with independent specialists. Best of both worlds.
Emerging Protocols
Three standards are shaping interoperability:
| Protocol | Origin | Purpose |
|---|---|---|
| MCP | Anthropic | Standardized tool/resource access |
| A2A | Peer-to-peer agent collaboration | |
| ACP | IBM | Enterprise governance framework |
OpenClaw's model-agnostic architecture positions it well for multi-protocol futures.
The Trust Paradox
Counterintuitively, executive confidence in autonomous agents has dropped:
- 2024: 43% confident
- 2025: 22% confident
- 60% don't fully trust agents for autonomous tasks
As capabilities increase, trust decreases. This creates opportunity for builders who prioritize transparency and security.
How to Think About OpenClaw's Future
Near-term (2026):
- Multi-agent skills emerge on ClawHub
- MCP integration deepens (mcporter already started)
- Security tooling matures around AGENTS.md auditing
Medium-term (2027-2028):
- Agent-to-agent protocols standardize
- "Internet of Agents" architecture crystallizes
- Enterprise adoption accelerates with governance
Long-term vision: OpenClaw is infrastructure, not product. Its minimal 4-tool core and model-agnostic architecture suggest personal AI infrastructure becomes standard—orchestration layers matter more than individual agents.
Quick Reference: Do This
For Beginners
- Use DigitalOcean 1-Click Deploy
- Configure AGENTS.md before connecting channels
- Run
openclaw healthliberally - Keep workspace in private git repo
For Production
- Implement all three threat vector mitigations
- Route integrations through managed authentication
- Use Tailscale for network isolation
- Audit AGENTS.md configurations regularly
For Future Builders
- Design for multi-agent orchestration
- Build composable skills
- Watch MCP/A2A/ACP protocol development
- Contribute to security tooling
The Bottom Line
Running OpenClaw well requires understanding it's infrastructure, not a product. Best practices aren't features to enable—they're threat vectors to mitigate.
The 180,000 developers who installed OpenClaw proved demand exists. The ones who configure it securely will define what personal AI infrastructure looks like.
The multi-agent future is coming. Build accordingly.
Sources: OpenClaw Documentation | DigitalOcean Deployment Guide | Deloitte AI Agent Orchestration Report
Written by
Global Builders Club
Global Builders Club
If you found this content valuable, consider donating with crypto.
Suggested Donation: $5-15
Donation Wallet:
0xEc8d88...6EBdF8Accepts:
Supported Chains:
Your support helps Global Builders Club continue creating valuable content and events for the community.